Microsoft Nps Radius Ports
In this article I will go through the steps required to implement RADIUS authentication using Windows NPS (Network Policy Server) so that firewall administrators can log-on using domain credentials.
Microsoft Network Policy Server RADIUS Server. This template assesses the status and overall performance of a Microsoft Network Policy Server (NPS) configured as a RADIUS server. Apply this template if you have NPS installed as a RADIUS server. WMI access to the target server. Windows Administrator on the target server. During the planning for NPS configuration, you can use the following steps. Determine the RADIUS ports that the NPS uses to receive RADIUS messages from RADIUS clients. The default ports are UDP ports 1812 and 1645 for RADIUS authentication messages and ports 1813 and 1646 for RADIUS accounting messages. RADIUS: To create policies for 802.1X wired or wireless with a wizard, Creating a Policy in NPS to support PEAP authentication. Open the Network Policy Server console. Navigate to NPS(Local)PoliciesConnection Request Policies. Right click Connection Request Policies and select New. On Specify Connection Policy Name and Connection Type enter a Policy name: and click Next. By default, NPS sends and receives RADIUS traffic by using User Datagram Protocol (UDP) ports 1812, 1813, 1645, and 1646. Windows Firewall on the NPS server is automatically configured with exceptions, during the installation of NPS, to allow this RADIUS traffic to be sent and received. Trying to setup Windows Server 2019 as a RADIUS server. However, after configuring everything, 'netstat -b' shows that the machine is not listening on any of the expected RADIUS ports (1812, 1645, 1813, 1646). Installed the 'Network Policy and Access Services' role; Followed the 'Configure VPN or Dial-up' wizard Confirmed RADIUS configuration.
My Setup
- Palo Alto running PAN-OS 7.0.X
- Windows Server 2012 R2 with the NPS Role – should be very similar if not the same on Server 2008 and 2008 R2 though
- I will be creating two roles – one for firewall administrators and the other for read-only service desk users.
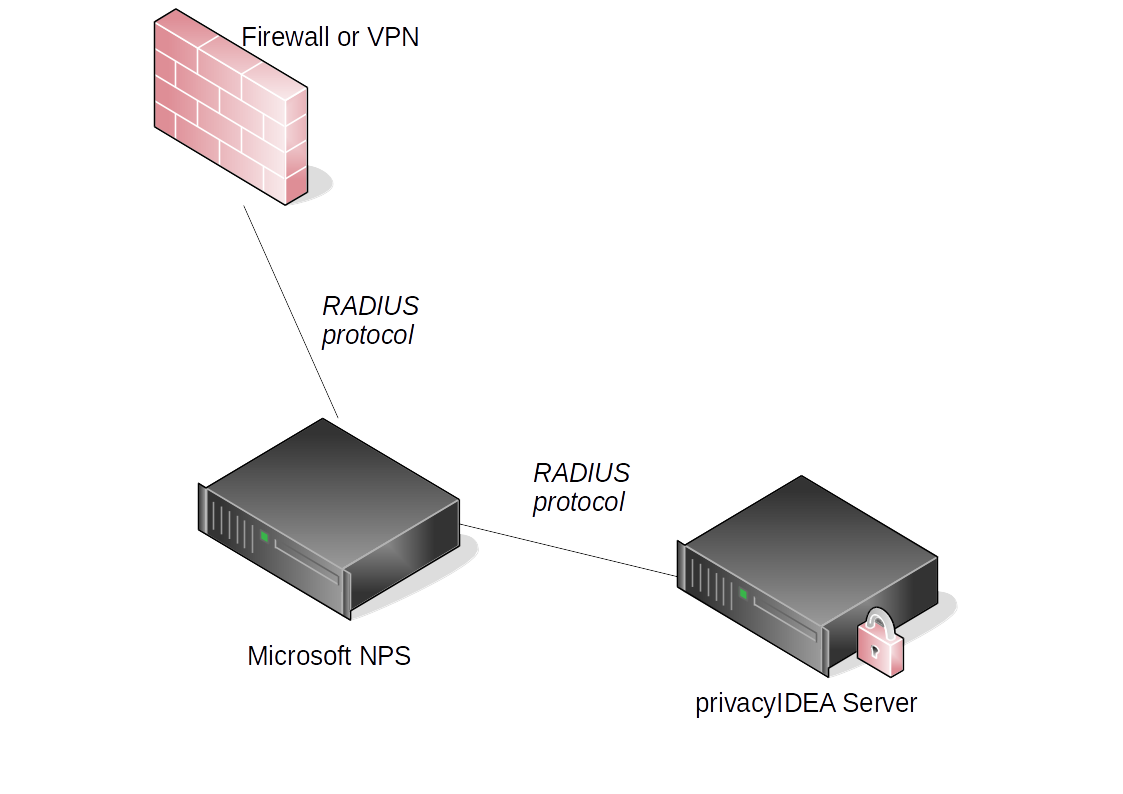
NPS Configuration
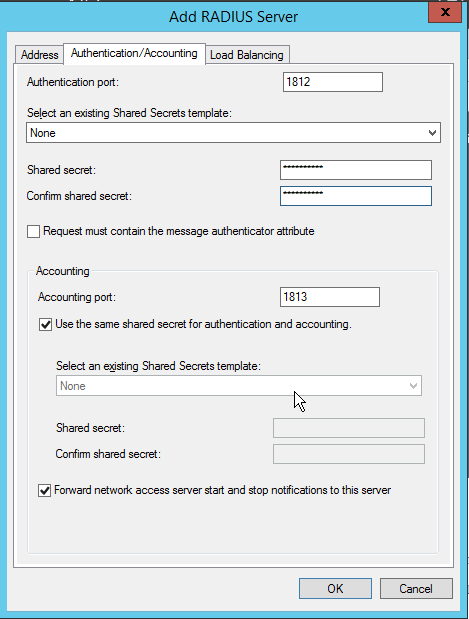
First we will configure the NPS server.
- Create the RADIUS clients first. The clients being the Palo Alto(s). If you have multiple or a cluster of Palo’s then make sure you add all of them. You don’t want to end up in a scenario where you can’t log-in to your secondary Palo because you forgot to add it as a RADIUS client. Make a note of the generated secret key as you will need it later on.
- Next create a connection request policy if you don’t already have one. A connection request is essentially a set of conditions that define which RADIUS server will deal with the requests. In my case the requests will come in to the NPS and be dealt with locally.
- Now we create the network policies – this is where the logic takes place.
Now let’s configure the Palo…
Palo Configuration
First we will configure the Palo for RADIUS authentication. This involves creating the RADIUS server settings, a new admin role (or roles in my case) and setting RADIUS as the authentication method for the device.
Note: Don’t forget to set the Device –> Authentication Settings –> Authentication Profile on all your Palo’s as the settings on these pages don’t sync across to peer devices.
Other tips
Nps Radius Certificate
- It is good idea to configure RADIUS accounting to monitor all access attempts
- Change your local admin password to a strong, complex one
- Monitor your Palo system logs if you’re having problems using this filter:
[code]( eventid eq auth-success ) or ( eventid eq auth-fail )[/code]
Microsoft Nps Radius Portsmouth
Related posts:
